Uncover Live Exploitation Activity and the IPs Behind it for Faster Threat Response
Real-time threat intelligence that cuts through the CVE noise.
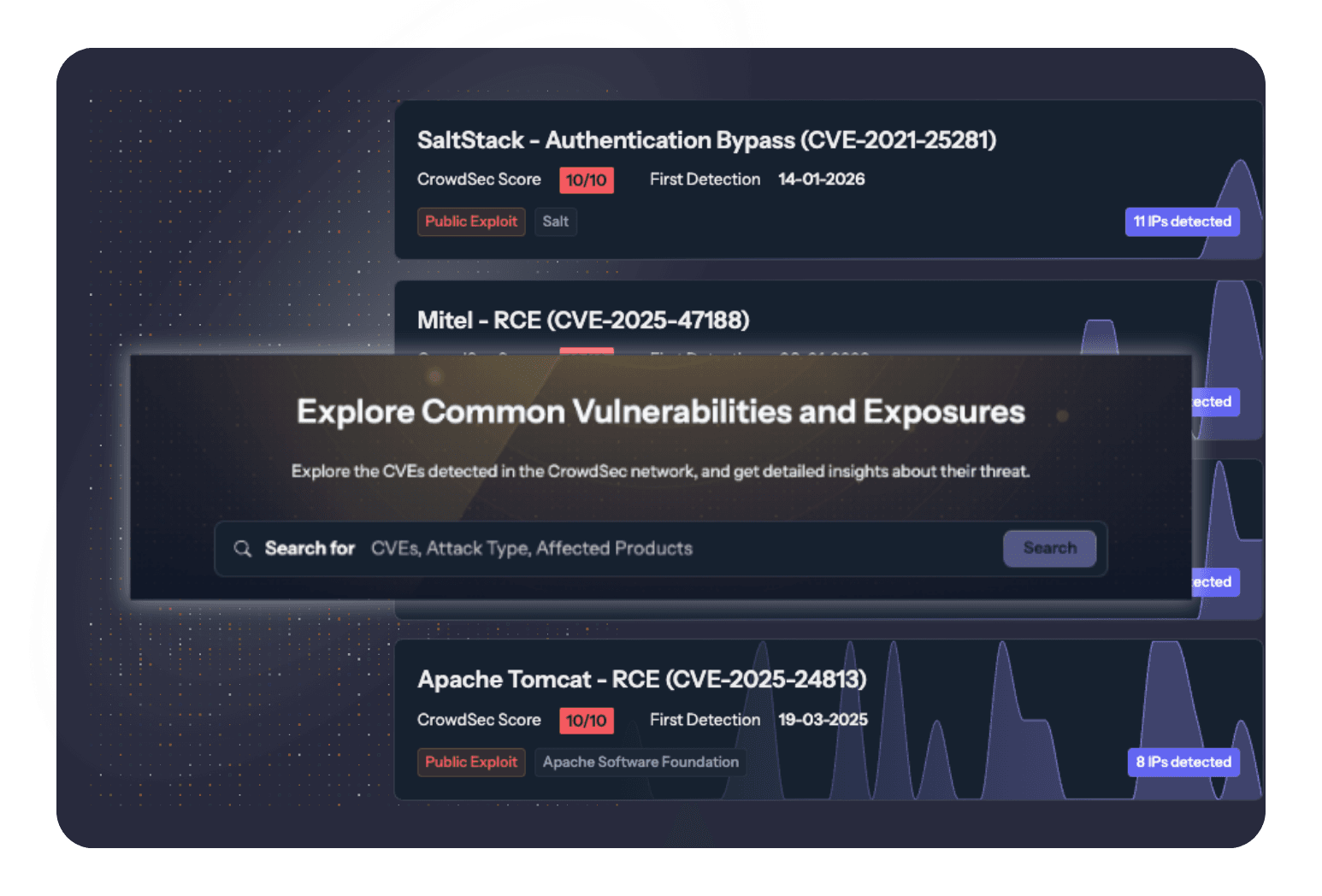

Gain Complete and Unquestionable Visibility into What’s Actively Being Exploited in the Wild
Live Exploit Tracker delivers observational, ground-truth intelligence based on live attacks seen across hundreds of thousands of production systems worldwide.
CVSS, EPSS, CVE, and KVE scores estimate likelihood. Live Exploit Tracker shows reality.

Prioritize What Actually Matters
Few CVEs are actual emergencies, but they are deadly. The Live Exploit Tracker reports real-world exploitation, enabling you to triage and patch vulnerabilities that are currently exploited in the wild.

Mitigate Attacks Simpler and Faster
Get a continuously updated list of IPs actively exploiting a given CVE, usable as a raw TI feed or as an edge-consumable blocklist format.

Anticipate the Next CVE
Track reconnaissance targeting specific vendors/technologies, including pre-CVE activity that is sometimes observed weeks before disclosure, so that you can harden your defenses earlier.


Why Live Exploit Tracker is Different

Production-Grade Intelligence
Live Exploit Tracker stands out with crowd-sourced intelligence, real-time IP data updated multiple times per hour, and edge-native outputs for Cisco, AWS, Fortinet, Cloudflare, iptables, and more. It even gives preemptive visibility into reconnaissance before CVEs are public, showing the full attack lifecycle so you can spot brief testing versus sustained campaigns.
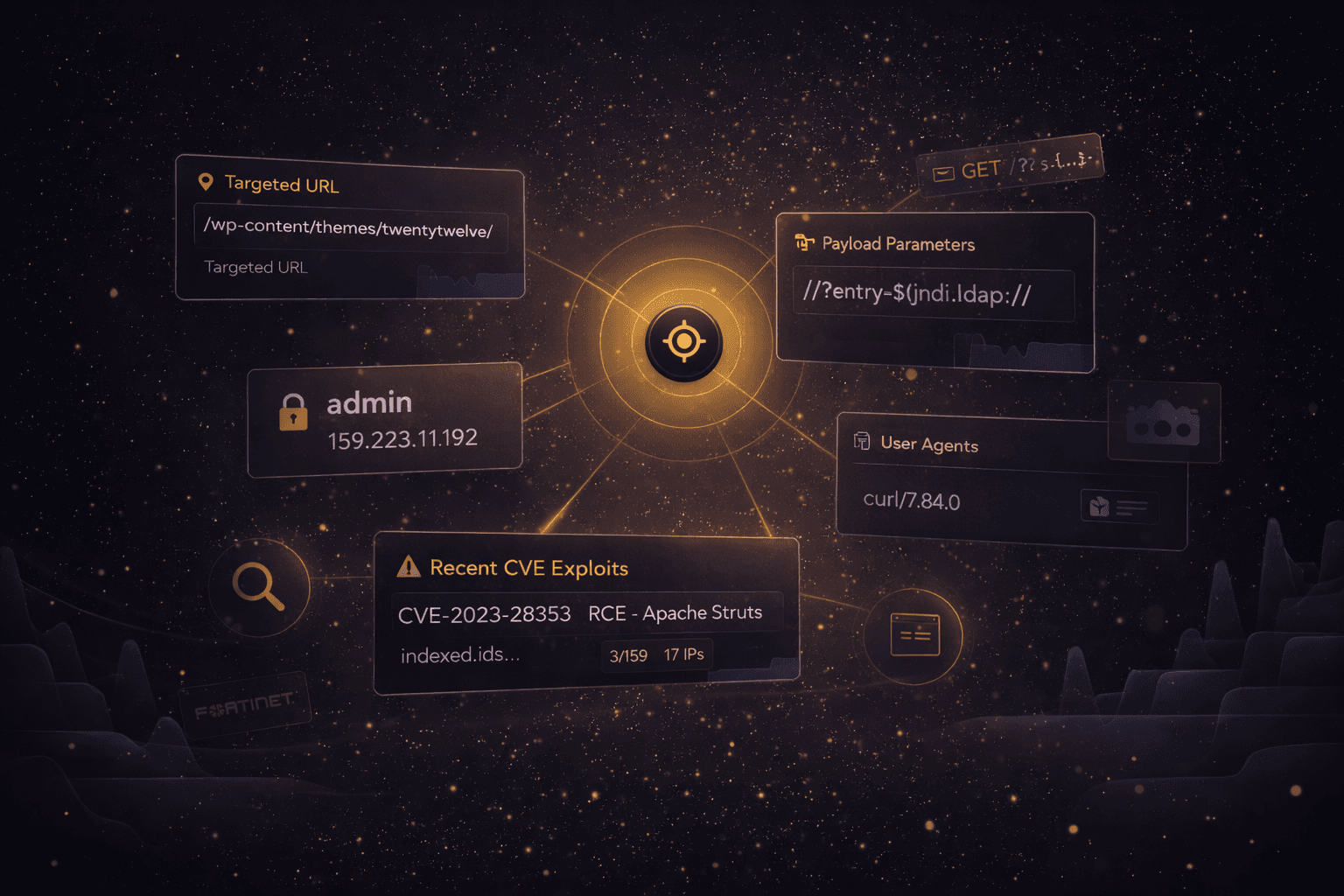
Unique IoC visibility
Live Exploit Tracker is fueled by real production telemetry, providing unique visibility into the indicators of compromise (IoCs) attackers use during active exploitation, such as targeted URLs, exploit payloads, credential patterns, user agents, and more. Live Exploit Tracker signals help you to classify exploit campaigns faster and design a sharper response to exploitation attempts before they escalate.
Learn more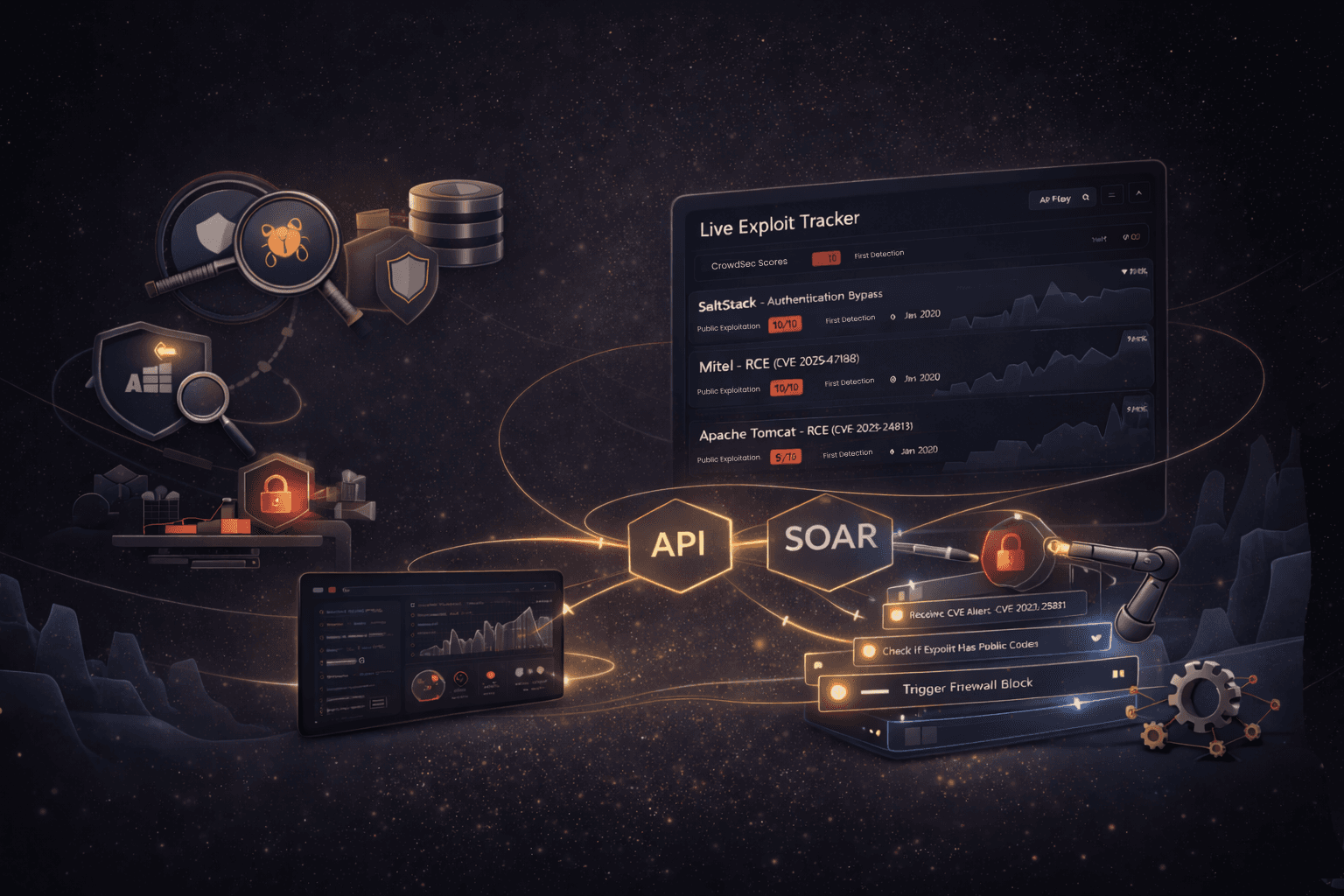
Actionable by design
Live Exploit Tracker is built for immediate operational use. You can pull exploitation intelligence via API and route it directly into your tools (e.g., SIEM/SOAR) to enrich alerts, trigger automated playbooks, and prioritize responses based on what’s being exploited right now. Whether you’re correlating events, accelerating triage, or driving automated mitigations, LET turns real-world exploitation data into actions your stack can execute.
Key Features & Capabilities
Live Exploit Tracker Score
A composite score built from observed exploitation factors like profile (opportunistic → targeted), scale, timeline, and intensity, plus top targeted countries per vulnerability.

Exploit IP Feed (per CVE)
A continuously updated list of IPs exploiting a specific CVE, refreshed multiple times per hour, with IPs added/removed based on recent activity.
Pre-CVE Scouting
List of IPs probing a vendor/technology over the last ~36h, including campaigns hunting for “unknown CVEs.”
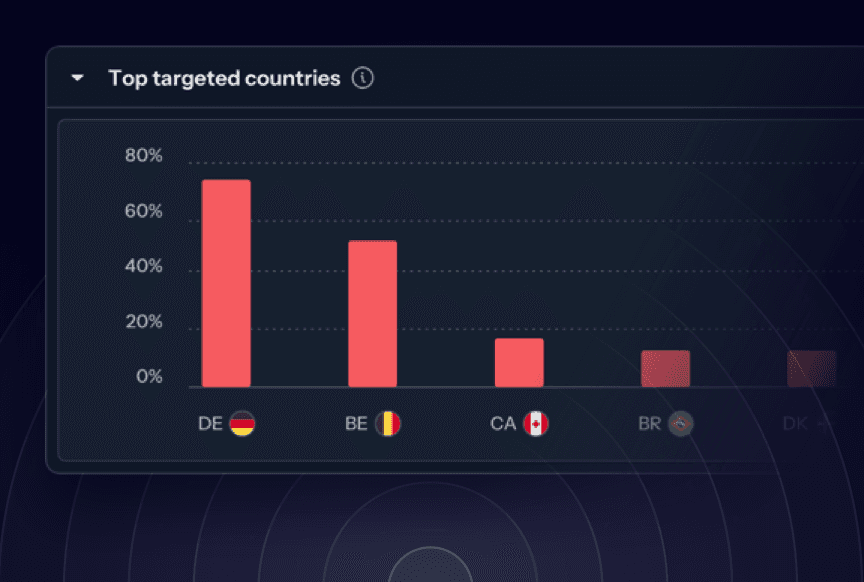
Top Targeted Countries
Understand geographic targeting trends per vulnerability to improve threat modeling, align defenses with attacker focus, and support geopolitical risk assessments.


Ready to Cut Through the CVE Chaos?
Contact our sales team to unlock all the features: IoCs, IP lists, and more.

Explore the CrowdSec Products

Security Stack
CrowdSec’s behavioral solution against targeted attacks consists of the Console, Security Engine, Remediation, and AppSec Components. Adapt and configure the CrowdSec Security Stack to fit your IDPS or WAF needs.
Get started
Blocklists
Block mass exploitation attempts before they reach your perimeter and get immediate protection against active malicious IPs with CrowdSec’s ultra-curated, actionable, and real-time blocklists.
Get started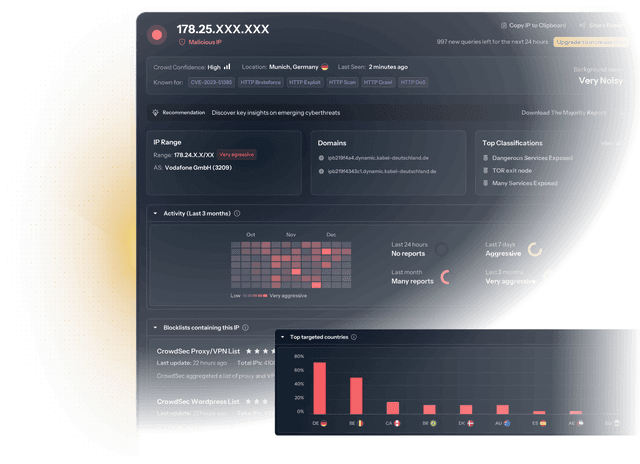
CTI
Access the most advanced real-world CTI distributing IP reputation intelligence that helps you detect, investigate, and respond to cyber threats more effectively and efficiently.
Try for free